17.12.25
Insurance Data Security: Risks and Solutions for Insurers

More than 60 percent of American insurers have reported at least one cyber incident in the past two years, shaking confidence in their ability to safeguard sensitive data. With cyber threats and data breaches growing more sophisticated, insurance organizations face urgent pressure to defend private information at every layer. This guide explains how modern data protection strategies keep American policyholder data secure, while helping insurers avoid costly mistakes and meet strict regulations.
Table of Contents
- Defining Insurance Data Security Fundamentals
- Types Of Data Insurers Must Protect
- Essential Data Protection Measures In Insurance
- Key Regulatory Requirements In Central Europe
- Common Risks And Costly Mistakes To Avoid
Key Takeaways
| Point | Details |
|---|---|
| Comprehensive Data Security | Insurance data security involves a multi-layered defense strategy that integrates technology, protocols, and risk management for effective protection. |
| Vulnerable Data Types | Insurers must prioritize the protection of personal identifying information, financial records, and institutional data to prevent significant consequences from breaches. |
| Organizational Policies | Implementing rigorous employee training and robust organizational policies is crucial for mitigating human error and enhancing overall data security. |
| Regulatory Compliance | Insurers must stay informed about evolving data protection regulations like GDPR and DORA to ensure compliance and safeguard sensitive information effectively. |
Defining Insurance Data Security Fundamentals
Insurance data security represents a comprehensive framework designed to protect sensitive information within the insurance ecosystem. At its core, this practice involves safeguarding digital and physical assets against unauthorized access, potential breaches, and sophisticated cyber threats. Data security in insurance goes beyond simple protection strategies, encompassing a holistic approach that integrates technological solutions, robust protocols, and strategic risk management.
The fundamental components of insurance data security include multiple interconnected layers of defense. Cybersecurity risk management practices critically evaluate technological infrastructures, ensuring the confidentiality, integrity, and availability of critical insurance data. These practices typically involve comprehensive authentication mechanisms, encryption protocols, secure network architectures, and continuous monitoring systems that detect and respond to potential security incidents in real time.
Effective insurance data security requires a multi-dimensional strategy that addresses technological, human, and procedural vulnerabilities. This means implementing advanced technological safeguards alongside comprehensive employee training programs and rigorous organizational policies. Insurance organizations must develop adaptive security frameworks capable of responding dynamically to evolving cyber threats, understanding that security is not a static condition but an ongoing process of assessment, adaptation, and improvement.
Pro Tip – Security Assessment: Conduct comprehensive quarterly security audits that systematically evaluate your organization’s technological infrastructure, identify potential vulnerabilities, and update protective measures proactively before potential breaches occur.
Types of Data Insurers Must Protect
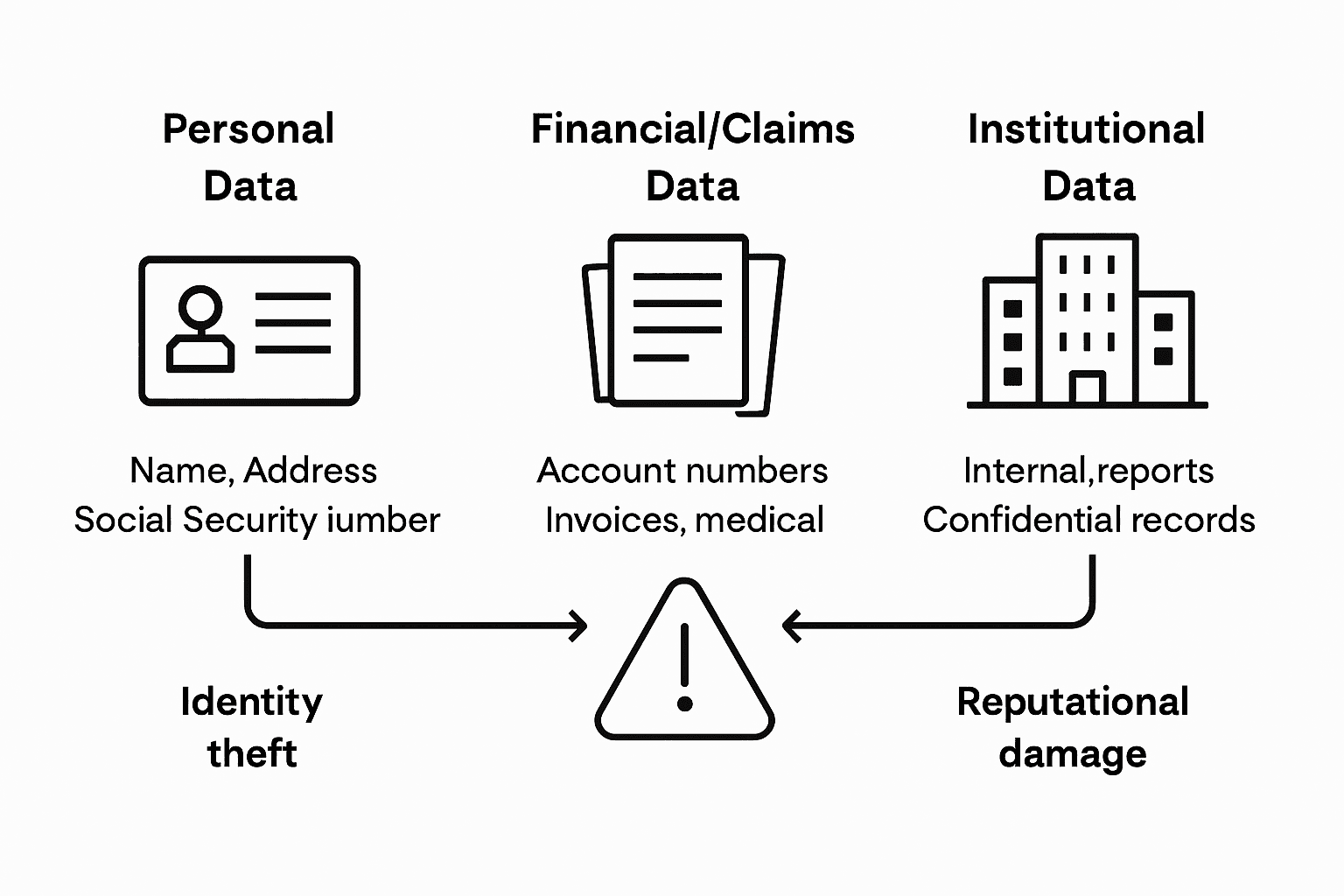
Insurance organizations handle a diverse range of sensitive data types that require meticulous protection and strategic management. Personal identifying information represents the most critical category, encompassing client names, addresses, social security numbers, birth dates, and contact details. This sensitive data forms the foundation of individual insurance profiles and demands the highest level of security to prevent potential identity theft or unauthorized access.
Key data management processes in insurance extend beyond personal identification to include comprehensive financial and risk-related information. These data categories include detailed financial records, credit histories, claims histories, asset valuations, medical records for health and life insurance, driving records for automotive insurance, and property assessments for homeowners insurance. Each data type requires specialized protection protocols that ensure confidentiality while maintaining accessibility for legitimate business operations.
Beyond individual client data, insurers must also safeguard complex institutional and transactional information. This includes internal operational data such as employee records, financial performance metrics, strategic planning documents, proprietary risk assessment algorithms, and confidential business communications. Cyber insurance practitioners utilize intricate datasets for underwriting and claims processing, making the protection of these computational and analytical resources paramount to maintaining competitive advantage and regulatory compliance.
Pro Tip – Data Classification: Implement a comprehensive data classification system that categorizes information based on sensitivity levels, enabling targeted security measures and precise access controls for different data types.
Here’s a summary of the main types of sensitive insurance data and why their protection is critical:
| Data Type | Typical Examples | Potential Consequences of Breach |
|---|---|---|
| Personal Identifying Information | Names, addresses, social security numbers | Identity theft, privacy violations |
| Financial & Claims Records | Credit histories, claims, asset valuations | Financial loss, fraud exposure |
| Medical & Risk Assessment Data | Medical files, risk profiles, driving records | Unlawful discrimination, misinformation |
| Institutional & Analytical Data | Employee data, algorithms, strategic plans | Loss of competitive edge, regulatory penalties |
Essential Data Protection Measures in Insurance
Effective data protection in insurance requires a multi-layered approach that integrates technological solutions, organizational policies, and robust security protocols. Encryption technologies form the foundational defense mechanism, transforming sensitive data into unreadable formats that prevent unauthorized access and potential breaches. Modern insurers must implement advanced encryption standards for data both in transit and at rest, ensuring comprehensive protection across digital communication channels and storage systems.

Data security measures necessitate comprehensive authentication and access control mechanisms that strictly regulate information visibility. This involves developing sophisticated user permission frameworks, implementing multi-factor authentication protocols, and creating granular access levels that limit sensitive information exposure. Insurance organizations should design role-based access controls that enable employees to view only the specific data required for their immediate professional responsibilities.
Technological safeguards must be complemented by rigorous human-centered security practices. This includes mandatory cybersecurity training programs that educate employees about potential threats, phishing techniques, social engineering risks, and best practices for data handling. Regular security awareness workshops, simulated threat scenarios, and continuous learning modules can transform staff into active participants in an organization’s data protection strategy. Additionally, insurers must establish clear incident response protocols that outline precise steps for addressing potential security breaches, ensuring rapid and coordinated reactions to emerging threats.
Pro Tip – Security Audit Frequency: Conduct comprehensive security audits quarterly, utilizing both internal assessment teams and independent third-party cybersecurity experts to identify and address potential vulnerabilities before they can be exploited.
Key Regulatory Requirements in Central Europe
Central European insurers must navigate a complex landscape of data protection regulations that prioritize individual privacy and organizational accountability. General Data Protection Regulation (GDPR) guidelines establish comprehensive frameworks for managing personal information, requiring insurers to implement stringent consent mechanisms, transparent data processing protocols, and robust privacy safeguards that protect individual rights throughout the insurance lifecycle.
The regulatory environment extends beyond basic data protection, introducing sophisticated operational resilience requirements. Digital Operational Resilience Act (DORA) regulations mandate that financial entities develop comprehensive cybersecurity strategies, including detailed incident reporting procedures, regular vulnerability assessments, and advanced technological infrastructure that can withstand and quickly recover from potential digital disruptions. These regulations compel insurers to move beyond passive compliance toward active, proactive security management.
Compliance in Central Europe demands a holistic approach that integrates legal, technological, and organizational perspectives. Insurers must develop comprehensive documentation demonstrating data handling processes, maintain detailed audit trails of information access and modifications, and establish clear governance structures that enable rapid response to potential regulatory inquiries. This requires creating internal policies that not only meet current regulatory standards but also anticipate potential future legislative developments in the rapidly evolving digital security landscape.
Pro Tip – Regulatory Mapping: Develop a dynamic compliance tracking system that continuously monitors regulatory changes, enabling your organization to adapt quickly and maintain ongoing alignment with emerging Central European data protection requirements.
Compare core regulatory frameworks governing insurance data security in Central Europe:
| Regulation | Main Focus | Key Requirement | Business Impact |
|---|---|---|---|
| GDPR | Personal data protection | Explicit consent, transparency | Strict privacy obligations |
| DORA | Digital operational resilience | Incident response, IT controls | Enhanced cyber risk management |
Common Risks and Costly Mistakes to Avoid
Insurers face a complex landscape of cybersecurity vulnerabilities that can lead to devastating financial and reputational consequences. Integration system security challenges expose critical weaknesses in platform architectures, revealing multiple potential entry points for malicious actors seeking to compromise sensitive insurance data. These vulnerabilities often stem from inadequate authentication mechanisms, insufficient third-party vendor risk management, and poorly implemented access control systems that create systemic security gaps.
Technological manipulation represents another significant risk vector for insurers. Adversarial data manipulation techniques demonstrate how sophisticated attackers can exploit seemingly secure systems, particularly in personalized insurance products like automotive coverage. Attackers may attempt to manipulate data collection devices, falsify risk profiles, or generate fraudulent discounts by creating artificial variations in tracked information, undermining the fundamental risk assessment mechanisms that insurers rely upon.
Human error remains one of the most consistent and dangerous risk factors in insurance data security. Employees untrained in sophisticated cybersecurity practices can inadvertently create massive vulnerabilities through simple mistakes like weak password management, falling for phishing attempts, or improperly handling sensitive digital documents. Organizations must recognize that technological defenses are only as strong as their least informed team member, necessitating comprehensive, ongoing security awareness training that transforms staff into active defenders of organizational data integrity.
Pro Tip – Risk Assessment: Implement a continuous risk assessment framework that combines automated vulnerability scanning, regular penetration testing, and comprehensive employee security awareness training to create a dynamic, adaptive defense strategy.
Strengthen Your Insurance Data Security with IBA’s Cloud-Native Solutions
The article highlights the growing challenges insurers face in protecting sensitive data against sophisticated cyber threats and regulatory demands such as GDPR and DORA. You understand that multi-layered defenses, encryption, continuous risk assessments, and employee training are critical to safeguarding personal, financial, and operational data. Yet managing these complex security requirements while accelerating product innovation and maintaining compliance can feel overwhelming.
Insurance Business Applications (IBA) offers IBSuite, a secure, API-first insurance platform designed to reduce these burdens. With built-in encryption, granular access controls, and seamless integration capabilities, IBSuite empowers insurers to modernize core systems and stay compliant with evolving Central European regulations. If you want to minimize cyber risks, automate security management, and respond rapidly to digital disruptions, explore how IBSuite can transform your data security strategy.
Ready to protect your data and accelerate digital transformation today Engage with experts who understand insurance security and compliance fully Book a Demo and discover how to secure every part of your operation with a trusted, cloud-native platform. Take the first step now at IBA Applications.
Frequently Asked Questions
What are the fundamental components of insurance data security?
Insurance data security involves multiple interconnected layers of defense, including cybersecurity risk management practices, comprehensive authentication mechanisms, encryption protocols, secure network architectures, and continuous monitoring systems.
What types of sensitive data do insurers need to protect?
Insurers must protect various sensitive data types, including personal identifying information, financial and claims records, medical and risk assessment data, and institutional or analytical data related to their operations.
What are some key measures for protecting data in the insurance industry?
Key measures include implementing encryption technologies, establishing strict authentication and access control protocols, conducting regular employee cybersecurity training, and developing clear incident response protocols to address potential security breaches.
What common risks do insurers face regarding data security?
Common risks include integration system security challenges, technological manipulation by cybercriminals, and human error, which can all undermine data security and lead to significant financial and reputational damage.
Recommended
- Insurance Data Security Best Practices for P&C Insurers
- Cloud Security and Compliance for Insurers: Navigating 2025 Risks – Digital Insurance Platform | IBSuite Insurance Software | Modern Insurance System
- Cybersecurity for Insurers, tools and best practices – Digital Insurance Platform | IBSuite Insurance Software | Modern Insurance System
- Insurance Risk Management Explained: Best Practices – Digital Insurance Platform | IBSuite Insurance Software | Modern Insurance System
- Crypto Trading Bot Security: Protecting Profits and Data